Internet financial crime are on rise in India. Credit card transaction in international places while owner is in India (Card swiped in NY, owner is in Versova), electronic transfer of money from bank account. In recent time there has been an increase in such cases in India and also reporting of such cases. Cyber security is a rising concern globally — for individuals, businesses and nations. Unfortunately, many either don’t take the threat seriously or aren’t doing enough to protect themselves from cyber crime. Awareness is the first level of defense against such scams. Prevention, to the extent possible, seems to be better than cure. In this article we shall make you aware of fraudulent credit card transactions, hacking of banking account cases,how can you be duped, and how to protect yourself and what to do if you are a victim.
Table of Contents
Credit Card Frauds, Bank Account Hacked
On 21 January, Raj Mohan, a Bangalore-based IT professional, noticed an SMS he had got from his bank on 19 January. Considering it came on a holiday, he had not paid much attention to the message earlier. It read that a transaction for $174 (about Rs.10,000) had taken place through his credit card. “I immediately informed my bank. They said they would investigate the matter.” (Livemint 4 Feb 2013)
- Rs 1 crore stolen from executive’s bank account (Times of India 2-Feb-2013) The money was transferred in 12 transactions from the victim’s bank account, Mulund branch, using Real Time Gross Settlement system. Within mere 45 minutes, Rs 1 crore was stolen from his account. The Mulund police admitted that they are so far in the dark on how the crime was perpetrated, though they suspect that Korane’s e-banking details such as username and password were stolen and used for the fraud.
- Clone crime: Owner in Mumbai, card used by cheats in US again (Times of India 6-Feb-2013), Global gang skims Indian credit card industry of Rs 30 crore in 2 months (Times of India 6-Feb-2013) : According to media reports, credit card issuing banks in India have seen Rs30 crore of unauthorized transactions by an international syndicate in the last two months. All top credit card issuers — ICICI Bank, HDFC Bank, Citibank, SBI Cards and Axis Bank — have been affected by these frauds.
Why only International Credit Card Transactions? How can the bank account be hacked ?
Why International Credit Card Transactions
In India, a user needs the cardholder’s name, expiry date and CVV number (the three-digit number on the back of your card) plus the online banking password or one-time password for online transactions. Internationally, the transactions are done on the basis of credit card information alone. Although fraudulent transactions in India have shrunk dramatically with the introduction of 3D security, the weak link is international transactions.
How can a back account be hacked
Cyber expert Vijay Mukhi explained that a bank account can be hacked in various ways. A user’s online banking username and password can fall “into wrong hands if stored on a computer, a cellphone or scribbled on a piece of paper. Hackers send out viruses to steal passwords from computers. They also dispatch spam emails, which ask for banking passwords.” (Ref Times of India Rs 1 crore stolen from executive’s bank account)
How can you be duped or Swindled?
Some of the ways in which one can be duped or swindled are as follows (Reference Times of India Swindler’s List (Feb 2013))
Skimming
One of the ways that credit/debit cards can be compromised at ATMs or points-of-sale machines is by using a skimming device. Card skimming involves the fraudulent copying of information from the magnetic strip of a credit or ATM card.
- In this scam,a pocket-sized scanner is usually attached over the card reader.
- After that,when a customer swipes a credit or debit card,the skimming device secretly records the cards information Alternatively,a fake POS machine is employed.This machine does not debit any cash from your account;instead it just gives you a fake bill,while also copying the data from the card’s magnetic strip
- The crooks later retrieve the device and use the information to create cloned cards,or to make online transactions
PHISHING
Most financial (banking,credit/debit card) hack attacks start with phishing ,a term used to describe an online scam where fraudsters steal a victims personal information by sending out emails that appear to have originated from legitimate financial institutions like banks
- These emails usually state that the user needs to urgently update or validate his account information after clicking on a link in the email.
- The information that is sought usually includes data such as usernames,passwords,bank account and credit card numbers,card expiry date,etc
- The link,however,leads the victim to a fraudulent website that looks very much like the banks original portal
- Once the user enters his details there,the scammer comes in possession of information that can then be used to carry out bank transactions.
Sometimes phishing emails also come with an attachment that automatically downloads malware onto computers.This malware could possibly record keystrokes and steal critical data like logins and passwords without the user knowing.This information is then automatically sent to the scammer via the internet whenever the malware finds an open internet connection
MALWARE at Point of Sale
Anti-virus companies recently discovered Dexter,a malware that targets Point of Sale systems at big-name retailers,hotels,restaurants and even private parking providers. Once installed on a POS,it can work like a skimming device,without any extra hardware. Dexter targets machines with access to large amounts of required data. The malware has reportedly infected systems running version of Windows including XP,Home Server,Server 2003,and Windows 7. At present,it is still unclear how Dexter gets into POS systems
PHARMING
A victim is sent to a fraudulent site by using a computer virus,which could possibly have originated from a phishing email. Websites are identified on the internet by way of their IP address.So whenever a user types in a URL,such as www.mybank.com,that address is translated into an IP address via a DNS server on the internet After a user visits a website for the first time,the DNS entry for that site is usually stored on his PCs local cache so that his machine does not have to keep accessing the DNS server for future visits
In pharming,a virus attacks the DNS cache and then modifies entries there so the user is utomatically led to a fraudulent site without him even knowing it.After that,its scamming as usual,where the user is prompted for his login and password. It should be noted that some pharming scams also attack the main DNS servers,but these cases are rare because these servers are usually wellprotected against such attacks
SOCIAL ENGINEERING
Social engineering involves a scam where the perpetrators interact with a victim in the guise of bank executives,insurance salesmen or utilities engineers.This interaction could take place over the phone or in person,where these skilled crooks ask for critical data after gaining the victims confidence. These executives usually promise the victim some sort of reward or financial benefit in exchange of the information. In some cases,social engineers start profiling their victims from information posted on their social networks and may often use the information gleaned from there to make first contact. Surprisingly,social engineering is one of the most predominant ways of initializing a scam.
How serious is the threat of cyber crime?
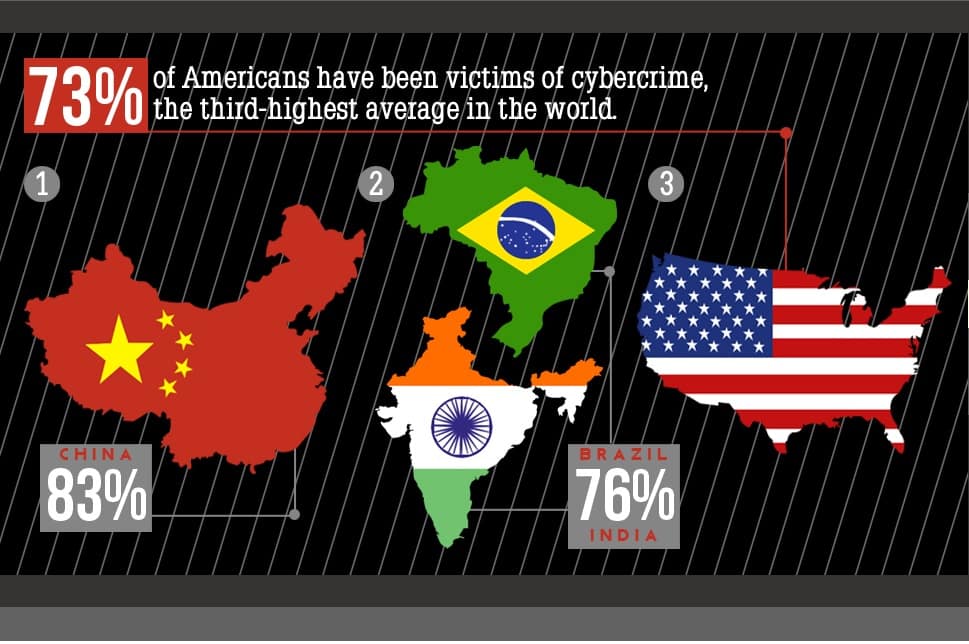
With threats looming everywhere from banks and web browsers to online dating and social networking sites, this might give you goosebumps. From Mashable 65% of Internet Users Are Cybercrime (Nov 2012) 65% of the global internet users have been victim of cyber crime either through viruses, online credit card or identity theft. The number across countries are:
Top 10 spookiest cyberattacks of the year 2012(till Oct) list of US companies was graced with big names such as Zappos, Amazon, LinkedIn and Android. If it can happen in USA then it can happen anywhere even in India.
How to avoid card and net frauds?
Some Do’s and Don’ts to avoid credit card and net frauds are given below(Reference : EconomicTimes Card Frauds may Impair RBI Effort to Popularise epay (8 Feb 2013)). Banks and card companies are also working in this direction. Also remember that It is riskier to swipe cards in Sri Lanka, Thailand, Philippines, Malaysia, and Indonesia than in Europe,. (Ref:Not safe to use cards in southeast Asia: Travel agents)
Passwords
Most people don’t put a lot of thought into creating a password. It’s usually easiest just to create a short, easy-to-remember password, or even just to use the same password for every account you have. While technically people are saving time by not needing to remember that much information, they might be gaining a good amount of trouble thanks to simple, often-repeated passwords. Thinking the average person probably won’t be able to guess your password won’t be of much help. Do you know people still creating their password with words like “password,” “123,” or “qwerty”? Most common passwords are 123456, abc123, password. Interested readers can checkout Infographic How strong is your password , How Common is Your Password?, Some common password mistakes are as shown by picture from GCFLearnFree.org Passwords: First step to safety (Click on image to enlarge)
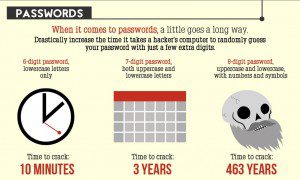
Password hacking is the process of recovering secret passwords from data that has been stored in or transmitted by a computer system. A common approach is to repeatedly try guesses for the password. Most passwords can be hacked by hashing, guessing, phishing or brute force techniques. By creating strong passwords, you can greatly reduce the chance that your personal or financial information will be stolen. What Makes A Strong Password. Picture below shows How much times it takes to crack a password?
Tips For Creating Strong Passwords
- Never use personal information such as your name, birthday, or spouse’s name. Personal information is often publicly available, which makes it much easier for someone to guess your password.
- Use a longer password. Your password should be at least six characters long, and for extra security it should ideally be at least twelve characters (if the site allows it).
- If you need to write down your passwords, keep them in a secure place. It’s even better if you “encrypt” your passwords or just write down hints for them that others won’t be able to understand.
- Don’t use the same password for each account. If someone does discover your password for one account, all of your other accounts will be vulnerable.
- Try to include numbers, symbols and both uppercase and lowercase letters (if the site allows it).
- Avoid using words that can be found in the dictionary. For example, “swimming1” would be a very weak password.
- Random passwords are the strongest. Use a password generator instead of trying to think of your own.
- Random passwords are harder to remember, so create a mnemonic device. For example, “H=jNp2#” can be remembered as “HARRY = jessica NOKIA paris 2 #.” This may still seem random, but with a bit of practice it becomes relatively easy to memorize.
- Instead of writing your passwords on paper where others can easily see them, you can use a password managerto encrypt and store them online. Some password managers can also generate random passwords, making your information even more secure. Examples of password managers include LastPass, KeePass, Firefox’s password manager, and Google Chrome’s password manager.
Reference : GCFLearnFree.org Passwords: First step to safety
What to do if you are victim?
You need to be careful while using credit cards for online transactions. Simple things like using a complicated password, being cautious about using your card in a secure computer environment and insuring your credit card can help reduces frauds. But what if, God forbid, you become the target your only way out is to get into a loop of justice-seeking that may take years together by which time the money you have lost would lose value and you would have done the running around that’s worth much more. A small relief is that your credit score doesn’t get affected. From Economic Times Are you a victim of credit card fraud? (Feb 2013) There are guidelines laid out by the regulator for banks to follow but
- it is not always easy for the victim
- It takes time to prove fraud and get the money reimbursed
- Be prepared for a struggle, as banks will try hard to limit their liability.
- In case of an online transaction, banks put the onus on the customer to prove that it was a fraudulent transaction.
- In case of multiple fraudulent transactions, banks want victims to share a part of the loss.
- You will have to be adamant with your bank in terms of getting your money back
From Hindustan Times Are you a credit card fraud victim?(Feb 2013) Here are the hoops you need to jump through before which you can expect justice. If you are lucky, you may not have to jump through all of them.
Step I: Inform the bank immediately and be firm
If you notice any kind of fraud transaction in your bank account, no matter how small the amount is, call or visit your bank as soon as you get to know about the fraudulent activity. If you are calling up the customer care, take note of the customer executive’s name and reference number. If you are submitting a physical letter, keep a copy for yourself. Similarly, keep the records if you send an email. There are instances, when the bank refuses to take the complaint, but some banks are cooperative.
Says Sanjay Sharma managing director and CEO, IDBI Intech Ltd, a wholly-owned subsidiary of IDBI Bank Ltd, “The moment a customer reports fraudulent activity on his card, the card is hotlisted after the due diligence so that no further fraud takes place.” Says Amit Sethi, chief information officer, Yes Bank Ltd, “If any kind of fraud happens the vigilance department is informed. If money transfer is involved, the account is freezed and immediately the process for tracing the money starts. In case money is transferred to another account fraudulently, the bank where the money is transfer is contacted and that account is also freezed. Same is the system if it happens at a point of sale or merchant. The bank contacts them too.”
Be adamant with your bank in terms of getting back your money. Says Murali Neelakantan, partner, Khaitan & Co, a law firm, “Individuals who have gone through such a fraud should stand up and say that they are not responsible for it. In fact, it is the bank that is at risk.”
Here you need to be vigilant in reading your transaction slip and credit card statements. Based on these documents, you can dispute with your bank.
Step II: Approach banking ombudsman
If you don’t get a reply from your bank within the specified period, or the bank rejects the complaint, or if the you are not satisfied with the reply, you can go to the banking ombudsman.
For approaching a banking ombudsman, you need to first check under which jurisdiction you fall (seehttp://rbi.org.in/commonman/English/Scripts/AgainstBankABO.aspx). Once you know whom to contact, you can either send an email, fax or letter to the ombudsman.
Usually, the banking ombudsman gives a ruling cases within 30 days. In case of fraudulent transactions and breach of security by the bank, the chances of getting justice are quite high.
Step III: Go to the appellate authority
If you are not satisfied with the ruling of the banking ombudsman and you have been unable to get your money bank, the next thing is to approach the appellate authority, who is RBI’s deputy governor; currently, KC Chakrabarty.
For this you will have to send a letter addressing Chakrabarty at RBI’s Mumbai office (seehttp://www.rbi.org.in/scripts/AboutusDisplay.aspx?pg=Departments.htm).
Step IV: Move the court
You can go directly to a criminal court. All you need to do is file a first information report or FIR at a police station.
You can also file a complaint with cyber police stations. Says Pawan Duggal, a cyber law expert, “Remember the Umashankar Sivasubramaniam case. Here an adjudicating officer ruled that the bank would have to pay around R12.50 lakh as compensation. In this particular case, the bank appealed to the Cyber Appellate Tribunal.”
Sivasubramaniam was a victim of phishing (online identity theft) in September 2007. He alleged the bank didn’t take any action and sued the bank under the Information Technology (IT) Act. As of now, the case is under trial.
There have been cases that have been disputed and solved and where a customer has got back his dues from the bank. But there are some that drag on for years together.
Related Articles :
In this article we shall make you aware of fraudulent credit card transactions, hacking of banking account cases,how can you be duped, and how to protect yourself and what to do if you are a victim. Be Aware! Remember Awareness is the first level of defense against such scams. Prevention, to the extent possible, seems to be better than cure. Have you been duped? Have you lost money due to credit card fraud or bank account being hacked or for some other reason. What did you do? How do you think one can be safe online? Will the cyber crime rise?







Today i got the call from one lady asking about my credit card number, she said refunding sum money to my this account when i asked from which bank ur calling than she tranfer to call another guy and he also asking my credit number, but not telling from which bank calling when i said not possible to give my number so started to abuse to me, This is the Numbers, 9136613862, 8743025942
Thanks!
Dear sir
Today my acount was hacked by mob no.0963183396 from my union bank acount,i request u 2 stop these activities.
Hello Sir
Mera Name Santosh Kumar Hain Kal Date 6 Agust Ko Mera A .T.M Card Dhoke Se Atm Me Badal Liya Aur Mere Account Se 105000 Se Nikal Liya Gya Hain Ye Hadsah Mere Sath Patna Jila Barh Ke A.T.M axix Bank Atm 9783 station road p.n.b me 11 baj kar 20 mint me hua hain jime 40000 hajar aur 38000 GCC . Main Barach S.B.I Barh Se Nikala Hain Aur Baki Ka Paisa 12000+15000 Account num 3500003207 Account holder Miss Kiran Devi Ke Accont pe Tranfer Kiya Hain
Sir Main Ek Bahut Garib Pariwar Ka hu Mera Jindi Bhar Ka Kamai Koi Chan Bhar Me Uda Le Gya Hain
Mujhe Maddat Ki Ati Awasakta Hain Krpya Sir Mera Madat Kare
Name Santosh Kumar
Father Name Rajo Das
Add Villege+Post Aunta Ps Hathidah
Disst Patna (Bihar)
Account Num 11671349150 S.B.I Aunta
Cont 9835248249/9122722247
thanks
Interesting article. I will share in the Inside Banking – Scams, Frauds and Crime LinkedIn group http://www.linkedin.com/groups/Inside-Banking-Scams-Frauds-Crime-4827067/about
Thanks!
Very very useful article.
At least steps give that victim can follow in case of any fraud is very informative.
This process can guide the victim on how to approach in this situation.
Thanks Jatin! I hope no one has to go through it but knowing what to do would help!
Once again a very good information on how to prevent fraud.
Thanks again.